
Abstract
Graphics Processing Unit (GPU) on smartphones is an effective target for hardware attacks. In this paper, we present a new side channel attack on mobile GPUs of Android smartphones, allowing an unprivileged attacker to eavesdrop the user’s credentials, such as login usernames and passwords, from their inputs through on-screen keyboard. Our attack targets on Qualcomm Adreno GPUs and investigate the amount of GPU overdraw when rendering the popups of user’s key presses of inputs. Such GPU overdraw caused by each key press corresponds to unique variations of selected GPU performance counters, from which these key presses can be accurately inferred. Experiment results from practical use on multiple models of Android smartphones show that our attack can correctly infer more than 80% of user’s credential inputs, but incur negligible amounts of computing overhead and network traffic on the victim device. To counter this attack, this paper suggests mitigations of access control on GPU performance counters, or applying obfuscations on the values of GPU performance counters.
About this work
Information Leakage from On-screen Keyboard
The GPU rendering of on-screen keyboard animation causes information leakage on user input.
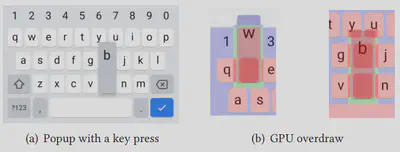
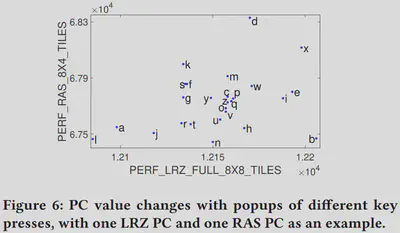
One-on-one mapping between key press event and GPU performance counter changes
Screen rendering activity is reflected by GPU performance counter values as provided by Qualcomm GPU driver via OpenGL APIs. The key pop-up activity has one-on-one mapping with certain GPU performance counter value changes.
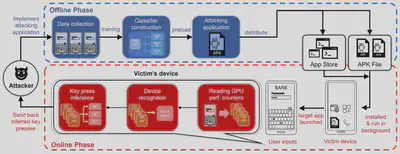
System Overview
Our work designs the whole attack with an offline training phase and online attacking phase. In the offline phase, the attacker emulates all key presses over different device models and configurations to collect a sufficient amount of GPU PC (Performance Counter) data. In the online phase, the attacking application will spawn a moni- toring process, which runs as an Android service in background. If a target application is launched, the monitoring process will start reading the selected GPU PCs. These readings will be first used to recognize the current device model and configuration, and then applied to the corresponding classification model for eavesdropping.
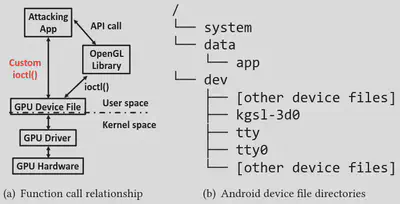
Reading GPU PC information from OS
We make use of customized ioctl() system call on GPU device file in the Android
OS in order to circumvent privilege limitation in system OpenGL library and directly
query system GPU performance counter values.
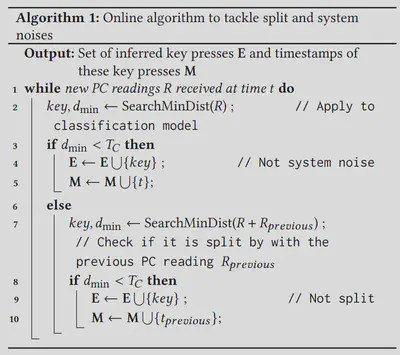
Handling Noises and System Factors
To reduce impact from noises and system factors, we use a distance-based algorithm to match the GPU performance counter readings with the nearest possible key press events.
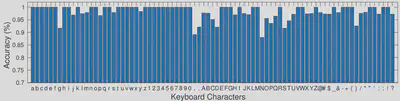
Key Press Inference Accuracy
With specially designed eavesdropping Android App, we can achieve an average accuracy of individual key press inference of up to 98.3%. For random text string inputs, the average inference accuracy is 81.3%.
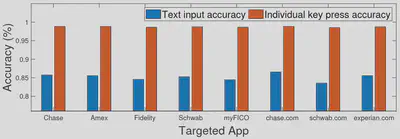
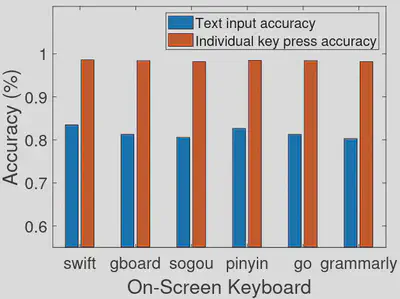
The inference accuracy is shown to be not significantly affected by the choice of targeted App or the on-screen keyboard software.
Follow-up Security Fixes
The vulnerabilities found in this paper is designated with CVE number CVE-2022-22075, acknowledged by Qualcomm Security Bulletin, and fixed in February 2023 Android Security patches.
